January '15 - Happy New Year (we hope)
Opinions, suggestions, recommendations or ideas found on our site are applied at your own risk. More.
If at first you don't succeed... So much for skydiving. Henny
Youngman
In this newsletter
- Slow Internet - sometimes?
- Windows Restore
- Quick run
- Windows 8.1 phone
- Just paranoia? We don't think so...
- Power cord recall

- Another recall we noticed
- Quick links
- It's about time
- Windows 8
- Phone bill
- Email "rules"
- Reminders and miscellaneous
- Pokki
- Don't believe it
Slow Internet - sometimes?
We recently had a computer in the shop that was causing all of the other computers on the customer's network to run slow. Initially we though it was infected but after some testing we found Dropbox was the culprit! So if you are using some sort of online sharing or backup system, you may want to check the application's options for time of day and/or bandwidth adjustments.
For Dropbox, we changed the bandwidth settings to limited. 50k download and 50k upload which resolved the problem. In Window's system tray, right click Dropbox, click the "gear" then select preferences. In that window you will see the bandwidth options...
Windows Restore
There are two main parts to Windows Restore:
- Restoring the system. This action should not affect any of your data. It can be used to bring the computer back to a specific date when it was working properly. Typically used after a file corruption, driver or update problem and in rare situations, it can be used to recover from a virus, but most viruses infect the restore points, so the computer is still infected afterward.
- Restoring individual files. This can be done on most any file on the computer. Used to recover from a corrupt file or perhaps one you change where those changes were not desired. Hint: If you want to experiment with data, wise to make a copy first.
For this newsletter, we're touching only on the individual file restore option; everything including a full factory restore is covered in our Windows Restore article. But you may want to see this information on creating a system image and/or a system repair disk for your computer, especially if you have neither.
|
Individual files may have shadow copies if the restore system is turned on and working properly, but restoring from your backup may be more efficient. To restore an individual file, you first need to locate the actual file. If you have only a shortcut you can right click the shortcut, select Open file location (or Open folder) then locate the actual file desired. Once the actual file is found, right click it, click to the Previous Versions tab and wait for the available restore points to appear (can take a moment or two). After the list is complete, simply select the desired date, click the "restore" button and cross your fingers.
|
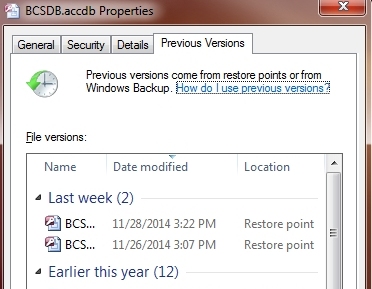 |
Notes:
-
This utility probably should be used only on data files. Programs have many individual files that are interdependent on other files and restoring one may further corrupt the program. Instead of attempting a program file restore, your better bet is to do a "repair" from Programs and Features or just reinstall the program.
-
Data files may also be interdependent so again, care needs to be taken. Accounting data files almost certainly fall under this situation. Many have individual data files for AP, AR, GL, etc., so restoring just one will corrupt everything. In the case of accounting applications, use the program's backup/restore system (and back up often using that utility).
|
 |
Our batch file backup may also be of interest...
Quick run
The keyboard's Windows key (lower left) can be a powerful ally! How to use: Hold it then touch another key once.
Used in combination with certain other keys, it can quickly get you where you want to be. Example Windows key+D minimizes all applications and shows the Desktop. Under Windows 8, it will bring you to the Desktop regardless of where you're at. See this article for Windows 8 application shortcuts and this article for a list of Windows 8 Window keys.
But with that said, Windows + R for the run command...
|
The Windows key + R or Run from the Start menu you can quickly start a variety of Windows utilities and even some of your regular applications. Run is not case sensitive so either MSRA or msra... msra may not be the best example. That is the Windows Remote Assistance utility but this particular utility is usually blocked by router firewalls. join.me is probably a better solution.
|
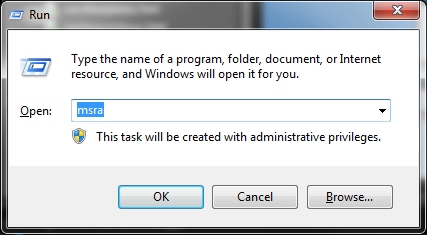 |
Just some examples, for a larger list see this article.
- calc - the calculator (much improved in Windows 7 and later, see also Calculator for even more hints)
- documents - opens your document folder
- pictures, favorites, video, music and recent will open those folders
- logoff - logs you out of Windows (but Windows key+L is even quicker)
- mip - math input panel (kind of interesting but handier for touch screen devices)
- notepad - similar to wordpad but edits in plain text only
- osk - opens the on-screen keyboard
- sdclt - Windows built-in backup utility (but see also backup batch file)
- snippingtool - built-in image snipping tool
- winword - Microsoft Word if installed
- the other MS Office applications (if installed): excel, msaccess, powerpnt, outlook
- wordpad or write - a basic word processor included with Windows. A bit more powerful than notepad but nowhere near as good as winword.
Windows 8.1 phone
In order to use Cortana (Microsoft's Siri) on our phone, we would have to allow Microsoft access to: Voice input (obviously) but also email and text information, contacts, browser search, calendar details and more.
The concern is access to the calendar and contacts details. These may contain information that should not be anywhere but in our hands. So if we did agree to use the service and some Microsoft employee decides to go rogue, where might our information end up? Just saying...
Just paranoia? We don't think so...
A prominent cyber-security company says it has uncovered evidence that suggests Sony Pictures was hacked by a team of six that was led by a dismissed company employee. The article.
Power cord recall
If you own a Lenovo notebook, you should visit their recall page and see if your machine is affected: http://support.lenovo.com/il/en/powercord2014
Another recall we noticed
Please, anything but coffee!!!
Keurig recalls over 6.6M coffee
makers due to burn risk
The article.
Geez, we didn't realize just how many recalls there really are. Here's the beginning of the list.
Quick links
A wearable computer. Pretty interesting but you'll probably need to shave first! YouTube clip. Thanks, Kurt
German researchers discover a flaw that could let anyone listen to your cell calls. - The article.
It's about time!
Microsoft has declared war on a company misusing its trademarks
in a tech support scam, and it's seeking damages.
The Federal Trade Commission has taken on numerous US tech support scams
over the past years to tackle fraudsters claiming to be from
Microsoft, offering to help consumers remove viruses, spyware, and
system errors on their machines, but ultimately billing them for bogus
fixes.
The article.
Windows 8
If you hate having the "Charms" bar consistently appearing when your mouse happens to hit a corner, the Windows 8 Forum site has some registry tweaks that just may shut it off. See the "Option 1" area of that page...
Phone bill
Do a little checking on all those extra charges on your phone bill. Recently we had a customer point out that his phone bill included a franchise tax charge of $3.00 per month. But he lives in a township that doesn’t collect franchise taxes. With a call to Windstream and he was able to get a $60 credit.
Email "rules"
In Outlook and many other email clients (applications), you can set up rules to do the work for you. More information in our Outlook article, but here's one you may find handy...
|
Recently we've been getting email messages from blablabla@bla.click, .website, .xyz, etc. (and probably a lot more to come). Because the senders name changes with each message, blocking the "sender" does no good. Instead, set up a rule to move anything with that domain to the junk folder. Make sure to choose move and not move a copy... |
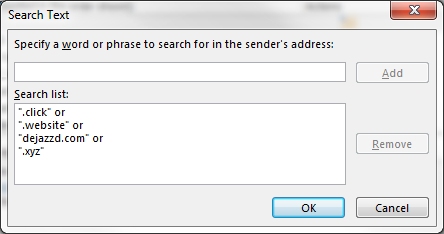 |
If you're really confident, you can certainly set the rule to delete the message instead of moving to junk.
Reminders and miscellaneous
Pokki
Perhaps an oddity or strange coincidence, but we recently restored a Windows 8 machine and with it, Pokki Start menu (and other Pokki items) restored as well. With this factory restore, we were unable to access the Google site, getting a page that read "nginx-use1a-04." There were no links and all other sites seemed to work just fine.
After uninstalling all the Pokki junk, everything seemed to work just fine again...
Don't believe it!
More important, don't click.
Opinion
WHAT??? Transportation for Obama to Los Angeles, California on October 9, 2014, for the Paltrow fundraiser cost taxpayers $1,011,051.30 The article.
Wow... Guess who said, "I’m Jewish in my soul"
Can we find more ways to waste "research" money? Article. (Imagine being in one during an earthquake!)
Leaving you with
The wit of Phyllis Diller:
- Housework can't kill you, but why take a chance?
- The reason women don't play football is because eleven of them would never wear the same outfit.
- The best way to get rid of kitchen odors is to eat out.
- We spend the first two years of our children's lives teaching them to walk and talk and the next fifteen years telling them to sit down and shut up.
- Cleaning a house with growing kids is like shoveling a walk while it's still snowing.
- The only time I ever enjoyed ironing was the day I accidentally put gin in the steam iron.
- Old age is when your liver spots show through your gloves.
- My photographs don't do me justice -- they just look like me.
- I had a pain beneath my left breast. Turns out it was a trick knee.
- Tranquilizers work best when you follow the advice on the bottle: “keep away from children.”
- The golf pro tells you to keep your head down so you can't see him laughing.
- You know you're old when your blood type is discontinued.
And we can't help but to show you one of the funniest stupidest email scams in a long time.
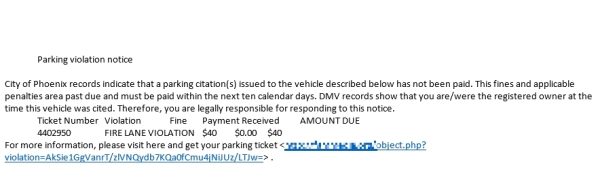
Remember...
SCAM: A "support" person asks you to allow
them to take over your computer and clean it up.
Just hang up! See our
October
newsletter for a bit more on this scam...
and

Thanks for all the help over these years, Jeff...