December '14
Opinions, suggestions, recommendations or ideas found on our site are applied at your own risk. More.
 |
Wishing all a very Merry Christmas
and a Happy New Year! or Season's Greetings if you prefer... |
 |
Due to the increased popularity of the scam, this will be our newsletter header for a while: Sorry, but you are simply not important enough to have Microsoft, Adobe, Java or anyone else call you about your computer. If you get a call that your computer is infected, compromised or otherwise needing attention, just hang up the phone!
More information here. So with that out of the way...
In this newsletter
- First off
- Windows Update
- Internet Explorer auto update
- Updates break Internet Explorer
- Speed up browsing notice
- iMess

- Stay safe
- Windstream help
- Virus that encrypts your data

- From the web
- From email attachments
- Protecting your data may be difficult!
- Hardware driver infection
- Make the recovery media as soon as you get a new computer!
- Google links
- Quick links

- Opinion
- Leaving you with
First off
Have a flashlight utility on your (Apple) phone? You may want to see this. Thanks, Gene!
Windows Update
It's fairly rare but sometimes Windows updates can cause problems with older programs.
|
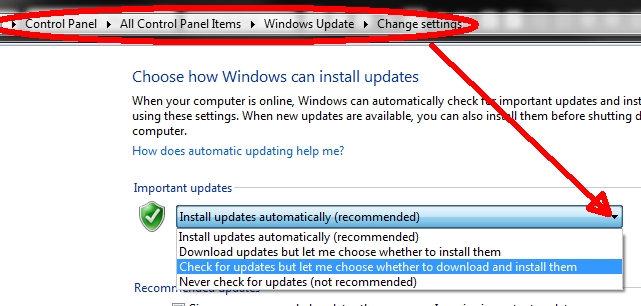
If you have confirmed this to be the case or have a
manufacturer recommend turning off automatic updates, here's
how
But do so only if necessary! To undo already installed updates, and for more information on updates. |
 |
Internet Explorer auto update
IE may automatically update even if the setting above is not to. See IE issues - Auto udpates
Windows updates break Internet Explorer
The updates installed automatically may break IE11 if you have Microsoft's EMET tool installed. Fortunately an easy fix, just uninstall then reinstall EMET...
Speed up browsing notice
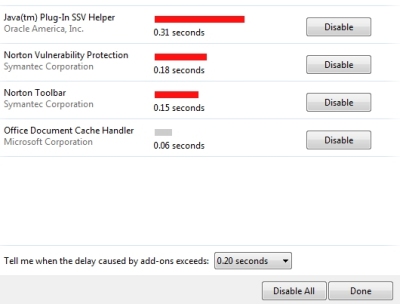
| If you're seeing the speed up browsing notice in the Internet Explorer, click the Choose button. |
|
|
When that window opens, you can: Change the notification warning period (near the bottom) to a longer period than the total of the add-ons listed. In this example .31+.18+.15+.06 = .70 so change the delay timer to a value longer than that. Or you can disable some add-ons. If you do disable some and find sites do not work correctly, simply re-enable the needed add-on... Also see IE Opens slowly. |
 |
iMess
The Internet is a mess!
According to some articles, the number of infected websites exceeds 1 million, so you really need to be careful out there!
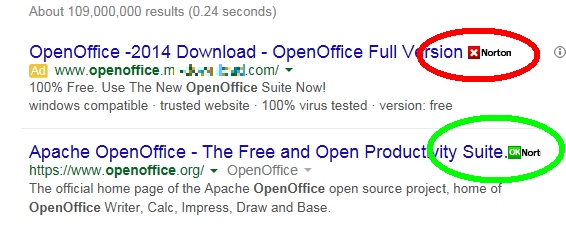
As we have discussed before, the search engine results will likely list sites you never want to visit. The following is a good example. While searching for OpenOffice.org, the very first result in Google is an infected site according to Symantec!
So one way to protect yourself is to use an antivirus that offers website ratings. But if you do have this service and decide not to heed the warning, be sure to call before dropping off the computer for repair. ;-)
In this example you can see that Norton/Symantec strongly disapproves of one site and approves the next (which is the proper site for OpenOffice). If search results reveal an orange/red approval icon, don't go there! If it's grey, be careful as the site is yet untested/unrated!
For that to work you must of course leave the protection enabled... See browser add-ons.
Stay safe
Review these Microsoft articles on various security issues:
- Avoid tech support phone scams
- How to recognize phishing email messages, links, or phone calls
- Safe Surfing
And if you want to tighten the Internet Explorer's settings, you could try these...
-
Fix Internet Explorer issues to make IE fast, safe and stableDiagnose and repair IE problems that make IE slow, not secure, unstable or crash, caused by add-ons not working or inappropriate security settings.
-
Automatically fix Windows security settings to keep your PC safeDiagnose and fix Windows security settings for IE, Windows firewall, group policy, Registry, UAC; check Windows Update and antivirus software status.
-
Fix security issues to protect and secure Windows automaticallyDiagnose and repair Windows security problems by turning on UAC, DEP protection, Windows firewall and other Windows security options and features.
Windstream help
If you end up at the wrong site, your screen may indicate Windstream Support has detected some sort of a problem and you are to call the number shown. DO NOT! Refer to our intro statement at the top.
If you really want to contact Windstream from the Annandale area, use the known good number of 274-8201.
Web pages can read all kinds of information from your visit including your IP address which then tells them who the provider is. They can then have the page impersonate that company.
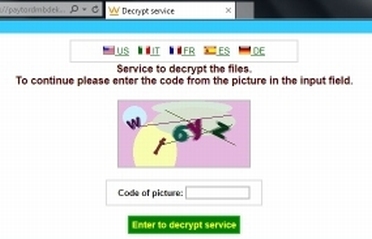
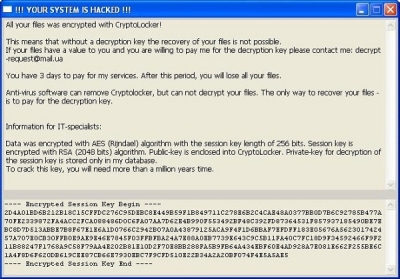
Virus that encrypts your data
Ransom viruses have been around for some time, but it's a first for us seeing one. Then suddenly we have seen five computers with virus encrypted data files in as many days. While the computers are repairable by formatting/reinstalling the operating system, the data could not be salvaged unless the owners were to pay a ransom to someone (overseas).
If you see anything similar to these on your computer, your data is already inaccessible. And typically all of your data: photos, documents, spreadsheets, email, contacts and so on.
|
|
 |
It's important the first
thing to do is terminate the network connection by turning
off
or disabling the wireless connection and unplugging the
network cable.
There are of course variations to the ransom viruses, with some coming in from Internet sites, others from email attachments. Various articles are indicating these viruses are network aware and can infect data on mapped network drives as well as the local drive. So, this is especially disturbing to businesses. The virus may add registry keys whereby any attempt to restore a previous version of a data file will cause immediate deletion of all shadow copies so you cannot use the Windows file restore option.
According to this ZDNet article, there may be help available using a free tool where you submit one of the encrypted files to a site and they will attempt to unencrypt it. If successful they will send you the unlock key for the rest of your files. However, the article goes on to indicate that some decryption attempts were unsuccessful.
Be leery of claims of unencrypting. It is estimated that standard desktop computing power could take 6.4 quadrillion years to break a 2048-bit encryption. If you want your data, you will probably have to pay. Interesting articles on encryption at Wiki and Digicert.
From the web
According to this Komando article (thanks, Steve), this virus has been found in advertisements on legitimate websites like Yahoo Finance and Sports, AOL, Match.com and dozens of others. But it is unclear if you have to actually click the ad, or if passing the cursor over the ad, or simply being on that web page would activate the virus. Here's a "mouse over" example. (If it did not switch pages, good, you may be one step ahead.)
One of our customers is certain it was from Facebook since that's the only online use for her computer.
From email attachments
This (very comprehensive) Bleeping Computer article indicates the danger of email attachments such as a phony FedEx, UPS, etc., failed or delivery notice and similar email scams, e.g., FORM_101513.pdf.exe. You must be especially aware of any attachment with an extension of .vbs, .bat, .exe, .pif and .scr as they are programs/applications that run and not simply documents for viewing. Because you may not see that second extension of .exe, you may want to review our extensions for more information page.
Protecting your data may be difficult!
The only way to be completely safe is to never connect to the Internet - ever, but short of that:
-
Suspect all email attachments regardless of who they are from. Most of us have seen emails from people we know but contained within is a single link to some website. Sender email addresses can be easily spoofed and sometimes completely hijacked and then abused.
-
Best practice for an email attachment is to turn off the Windows hide known extensions option (see this) and save attachments to the desktop (or another folder), then (right click) scan it with your antivirus before opening! Yes, that takes another minute or so to do, but it could take a week or more to recover from a ransom virus.
-
-
Make sure you have a good antivirus and it's up to date (although articles are indicating this virus is well along the process of encrypting your data before any antivirus detects what is happening).
-
Avoid domains (websites) that do not scan or inspect whatever third-party advertisements they accept, but knowing which domains are good about doing so is anyone's guess...
-
Follow the other "Stay safe" suggestions in our iMess section (above).
More information on this virus in this Symantec article and this PC World article.
We can't stress this enough - back up often and to multiple media!
However, it's certainly possible your backup system will back up already encrypted data so you need to be watchful for any problems, inaccessible data, new icons on the desktop and/or in documents folder, etc.
If you think you have been infected, immediately unplug or turn off/stop the backup system.
Hardware driver infection
Another new one for us, we had a computer that had a compromised wireless (WIFI) adapter driver. It was a very difficult and frustrating repair.
Basically, after clearing all the other problems, everything seemed ok, at least while connected to the Internet via the local area connection (network cable). But as soon as we connected wirelessly, the Internet was redirected to a site indicating the server was controlled by OpenX (even though the Address bar still showed www.google.com). More about that here if interested.
After a little more digging we found the Wireless adapter drivers had very recent dates. So we disabled the wireless adapter, reconnected the local connection then updated the wireless drivers from the device manager and all was good.
Make the recovery media as soon as you get a new computer!
Two recent machines with viruses could not be cleaned, and since the built-in recovery systems were also infected, every time the factory restore was complete, the computer was already infected!
In both cases we had to use recovery media (instead of the built-in), and in both cases we had to order the media from the manufacturer, causing a week plus delay in repair...
Aside: One was a Lenovo, which took 27 minutes to order (available by phone only), the other was a Dell, which took less than 2 minutes online.
Google links
We received what looked like an email message that had a google.com link, so we thought it was safe - WRONG!
Somehow a Google link that begins with http://www.google.com/webhp? (with more characters after the question mark) automatically redirects the browser to another site, so look out for these too...
We told you the Internet is a mess!
Quick links
While we don't do Facebook for a variety of reasons, here's an article about how you can be safe and secure in your Facebook travels. You may also want to see this article about a Facebook scam that one in three people fall for!
In reference to our previous conversation about the 2048-bit encryption; in perhaps just a few short years nothing will matter anyway! Interesting article on Quantum Computers. So what then for the future?
Apparently the Internet Explorer's SSL 3.0 security mode is a risk and Microsoft is recommending that option be turned off. That setting is found near the bottom of IE's Internet Options > Advanced tab or you can use Microsoft's FixIt utility found here: https://support.microsoft.com/kb/3009008#FixItForMe
Various "power saving" nuisance "features" in Windows, see power settings.
Here is what a trillion dollars looks like.
Opinion
How secure are you with our government?
Keeping in mind just how easily
government secrets and personal information gets out...
FBI director demands access to private cell phone data.
The article.
Anything to push the global warming agenda?
Biden overstates deaths in Joplin, Missouri tornado by 160,839 The article.
Someone please forward this to Al Gore: 50 States below freezing - including Hawaii. (but it's a terrible NBC site)
Out of control
The federal government made $20 billion in secret purchases including: $30,000 in Starbucks Coffee drinks and products in one year without having to disclose or detail the purchases to the public. The article.
and
Thousands of federal workers on extended paid leave - During a three-year period that ended last fall, more than 57,000 employees were sent home for a month or longer. The tab for these workers exceeded $775 million in salary alone. The article.
and
Southern United Neighborhoods and ULU Local 100, both rebranded ACORN entities, potentially misusing over $1.3 million of taxpayer dollars for union activities instead of enrolling individuals in the Affordable Care Act The article
and
President Obama’s Labor Day 2014 weekend trips for fundraising, personal business, and politicking came to a total of $1,539,402.10 in taxpayer-paid transportation expenses. The article
Leaving you with
There are 00110010 kinds of people in this world. Those that understand
binary and those that don't.
and from AL Lowe
You may need a new lawyer if:
- When the prosecutors see your lawyer, they high-five each other.
- During your initial consultation, he tries to sell you Amway.
- He tells you that his last good case was a "Budweiser."
- He picks the jury by playing "duck-duck-goose."
- He asks a hostile witness to "pull my finger."
- During the trial, you catch him playing games on his phone.
- Every few minutes he yells, "I call Jack Daniels to the stand!" and then drinks a shot.
- He gives the jury the finger.
- He places a large "No Refunds" sign on the defense table.
Remember...
SCAM: A "support" person asks you to allow
them to take over your computer and clean it up.
Just hang up! See our
October
newsletter for a bit more on this scam...
and

Thanks for all the help over these years Jeff...