January '19
Happy New Year!
Site information and disclaimers
PLEASE - Do not give control of your computer to ANYONE unless you are absolutely certain who they are! For more information see our Self Help > Scams!
In this newsletter
- Security issues
- Secure website padlock
- "Fileless" viruses
- UPNP
- Drive failures
- Think ahead - passwords, etc.
- HP ripping people off?
- Various issues
- Trouble with Google Chrome
- Bad Google apps removed
- Opinions
Security issues
Used to be, we would leave our doors, cars and garages unlocked. But as the world changed, so did our attitude about safety, so these days we are all a bit more careful about securing our belongings. Suppose a bit human nature, but we seem to be lacking this attitude when it comes to our computers, where convenience still outweighs security.
- We are reluctant in changing to strong passwords, making dictionary attacks easier.
- We allow the computer to save login information, which if hacked, can be abused.
- Some are still unwilling to protect their computers with a good antivirus application.
With those few reminders out of the way, let us brighten your new year with some recently read articles...
Secure website padlock
| Be aware, the padlock shown at secure sites has nothing to do with the site's safety or integrity! Rogue sites may very well use a secure site to try and fool you. The lock means ONLY that the information between the site and your computer is encrypted! The article. |
 |
"Fileless" viruses
This article discusses a variant of older viruses that essentially do not place a file on your computer, so during a scan, your antivirus application will find nothing. Instead, if it is successful, it will load into memory and then hide on removable drives and disks. Previous versions were loaded via phishing scams by email or rogue sites, but the injection method of a recent version is yet unknown. Scary!
"Users and especially businesses that still use removable media in the workplace should practice security hygiene," Trend Micro concluded. "Restrict and secure the use of removable media or USB functionality, or tools like PowerShell (particularly on systems with sensitive data), and proactively monitor the gateway, endpoints, networks, and servers for anomalous behaviors and indicators such as C&C communication and information theft."
Some of the following is probably a bit more extreme than need be, but Symantec Security Response encourages all users and administrators to adhere to the following basic security "best practices":
- Use a firewall to block all incoming connections from
the Internet to services that should not be publicly available.
By default, you should deny all incoming connections and only
allow services you explicitly want to offer to the outside
world.
- New authentic routers
are factory configured to disallow inward activity.
Always buy new, in-the-box routers. Not refurbished, not used.
- New authentic routers
are factory configured to disallow inward activity.
- Enforce a password policy. Complex passwords make it
difficult to crack password files on compromised computers. This
helps to prevent or limit damage when a computer is compromised.
- Refer to last newsletter's discussion on passwords.
- Ensure that programs and users of the computer use the
lowest level of privileges necessary to complete a task. When
prompted for a root or UAC password, ensure that the program
asking for administration-level access is a legitimate
application.
- This is that sometimes irritating "do you want to allow" message you may see on occasion, but if you suddenly see that message when you are not installing something or making changes, reply No.
- Disable AutoPlay to prevent the automatic launching of
executable files on network and removable drives, and disconnect
the drives when not required. If write access is not required,
enable read-only mode if the option is available.
- Autoplay is found in the Control Panel. Changing write privilege makes no sense for backup devices.
- Turn off file sharing if not needed. If file sharing
is required, use ACLs and password protection to limit access.
Disable anonymous access to shared folders. Grant access only to
user accounts with strong passwords to folders that must be
shared.
- Network Sharing center - Contrary to
Windows "recommendation"
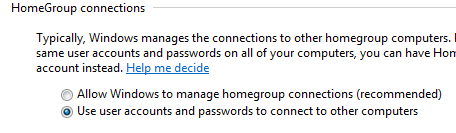
- Network Sharing center - Contrary to
Windows "recommendation"
- Turn off and remove unnecessary services. By default,
many operating systems install auxiliary services that are not
critical. These services are avenues of attack. If they are
removed, threats have less avenues of attack.
- Sorry, but there is no one rule or list for turning off services. Every machine's services will vary a bit depending on applications installed.
- If a threat exploits one or more network services,
disable, or block access to, those services until a patch is
applied.
- Unplug that machine from the network/turn off wireless or at least disconnect from the wireless network.
- Isolate compromised computers quickly to prevent
threats from spreading further. Perform a forensic analysis and
restore the computers using trusted media.
- Above.
- Always keep your patch levels up-to-date, especially
on computers that host public services and are accessible
through the firewall, such as HTTP, FTP, mail, and DNS services.
- Under Windows 10, patches and updates are automatic and unstoppable.
- Configure your email server to block or remove email
that contains file attachments that are commonly used to spread
threats, such as .vbs, .bat, .exe, .pif and .scr files.
- By default some email clients (applications) do this anyway. The list of dangerous extensions is a lot longer than that! See next item too...
- Train employees not to open attachments unless they
are expecting them. Also, do not execute software that is
downloaded from the Internet unless it has been scanned for
viruses. Simply visiting a compromised Web site can cause
infection if certain browser vulnerabilities are not patched.
- This is a tough one! Many if not most problems are attachments or links in email messages. Don't assume anything with attachments or links, no matter who they appear to be from.
- Always save attachments and scan with your antivirus before opening them. EVEN if they are from someone you know!
- If Bluetooth is not required for mobile devices, it
should be turned off. If you require its use, ensure that the
device's visibility is set to "Hidden" so that it cannot be
scanned by other Bluetooth devices. If device pairing must be
used, ensure that all devices are set to "Unauthorized",
requiring authorization for each connection request. Do not
accept applications that are unsigned or sent from unknown
sources.
UPNP
This article discusses how hackers have found ways to exploit a router's UPNP (Universal Plug and Play), effectively allowing a connection to devices and computers.
Log in to your router, look for and disable the UPNP option.
Drive failures
Again, we've been seeing some drive failures where data was not recoverable, at least without utilizing a (very expensive) service like OnTrack. Fortunately these recent few didn't have valuable data, but it gives us a chance to remind everyone to back up your data and to multiple devices.
- Better to take the time once a week or so and back things up rather than recreating data.
Aside: Out of pure maintenance, we replaced the hard drive on our main computer with a solid state drive (SSD), which is much quicker than traditional a mechanical drive (HDD). But like moving into a new computer, it took the better part of a day to (re)install everything, configure the system, printers and applications and the like.
If you're planning on a new computer, or replacing/reformatting your drive, don't forget to take into account everything that goes with it.
Think ahead - passwords, etc.
No one gets out alive so think of your successors/inheritors.
Have some sort of health directive for your computers/devices, starting with the computer's password to allow them access! But perhaps also a list of sorts, indicating where things can be found such as wills, tax information and the like.
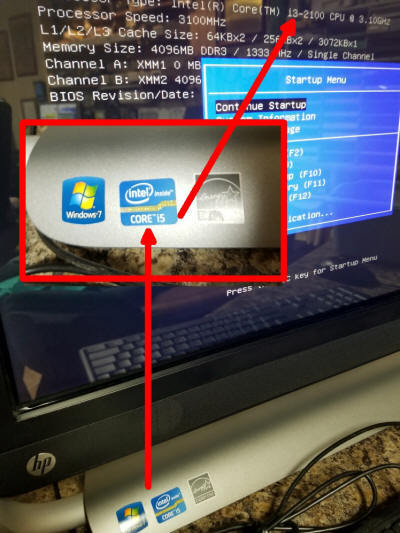
HP ripping people off?
Allegedly:
- Computer was ordered directly from HP.
- Computer never had work done (motherboard replaced).
This All In One (AIO) computer is labeled as having the Intel i5 processor, but the BIOS information screen shows the motherboard actually has the (much slower) i3 processor installed. We inform, you determine. (Sorry, Fox.)
Various issues
Google Chrome won't open in Windows 10?
- Browse to C:\Program Files (x86)\Google\Chrome\Application
- Select chrome (check it or left click it one time), then right click on it and select Properties.
- Click on the Compatibility tab. At the bottom, choose Change settings for all users.
- Check the box to Run this program in compatibility mode and set it to Windows 7.
Android apps that were removed from the Google store included simulations for driving a luxury car and a fire truck. All the apps were made by the same developer, Luiz O. Pinto. These apps were disguised as games, but they did not work when users tried to load them in order to play on phones and tablets. Instead, the apps would repeatedly crash but were still able to install malware. The article.
After
Microsoft complaints, Indian police arrest tech support scammers at
26 call centers.
The article.
If they could get scammers to repay the
people they ripped off, that would be meaningful!
Remember: If you see something on screen to
call a number or you receive a phone call indicating your computer
is infected, or otherwise needing you to call a support - it's
bogus!
Opinions
'True polar wander' may have caused ice age. The article. We had this observation last July but we followed the movement through to the present day. ;-)
Growing and harvesting bioenergy crops—corn for ethanol or trees to fuel power plants, for example—is a poor use of land, which is a precious resource in the fight against climate change, says a University of Michigan researcher. The article.
When the government provides everything, are higher taxes
unexpected? Come on, French people, wake up!
The article. Which brings a question for this country:
How much "green tax" are we willing to pay?
- To live in a metro area and where you would not need to travel.
- To not visit friends and relatives outside of walking distance.
- To give up:
- Cars, boats and other powered vehicles.
- Vacations (that requires travel).
- Air conditioning or any other powered creature comfort.
Let's face it, we are all willing to reduce our "carbon footprint"
but only to a point.
Leaving you with
It's a dangerous business going out your front door. - JRR Tolkien
And from Al Lowe
A duck stood beside a busy road, waiting for a break in traffic. A chicken walked up to him and said, "Don't do it, man. You'll never hear the end of it!"
Remember...

Thanks for all the help over these years, Jeff...